WORLD-LEADING ENTERPRISES LEAD WITH K2VIEW
In-flight and contextual
Give testers self-service access to the test data they need, instantly.
Referential integrity
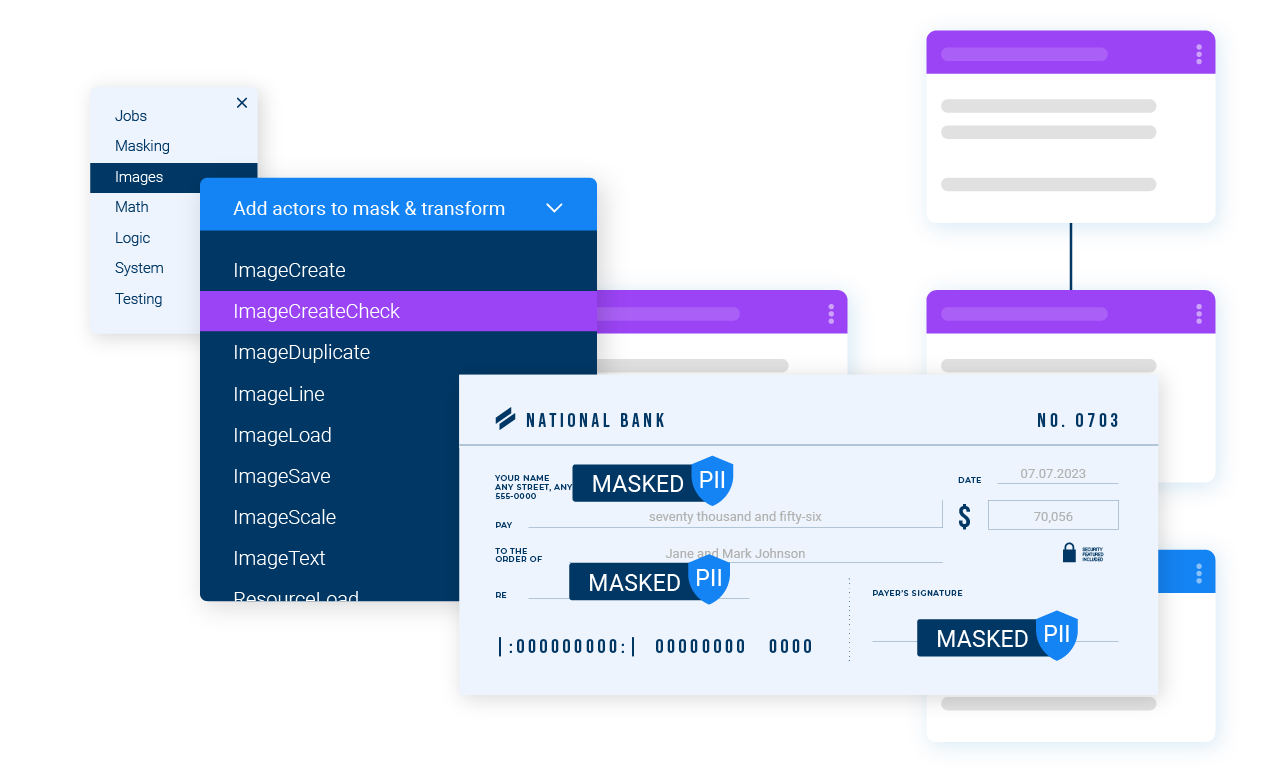
Entity data masking enforces referential integrity of the masked data, regardless of data source diversity.
Static and dynamic
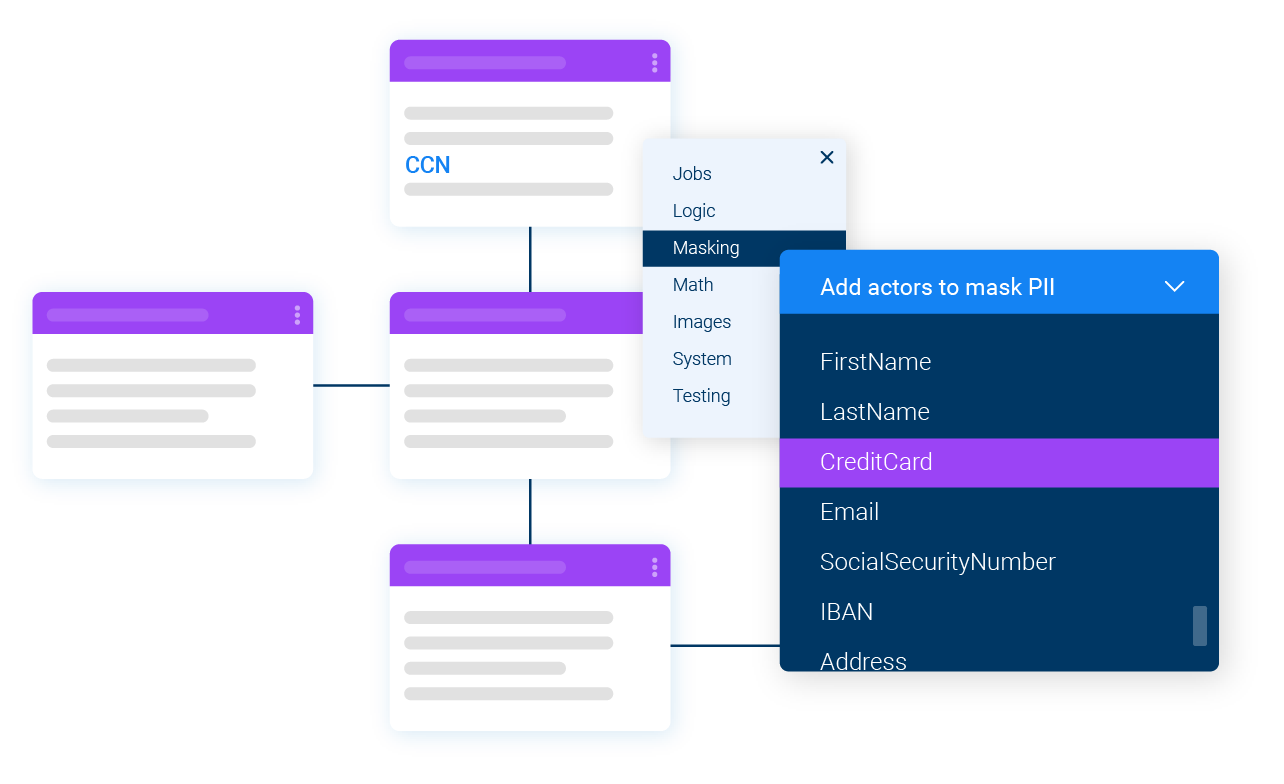
One tool for both static masking and dynamic masking, supporting any sensitive data use case.
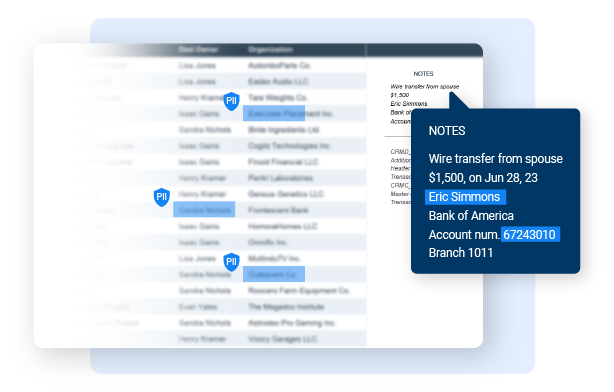
Auto-discover business entity schemas and auto-classify the PII and sensitive data for the business entities
K2view ingests multi-source data and automatically organizes it by business entities, in flight, to enforce referential integrity and contextual masking
Data is then masked in the context of the business entity and delivered to any target system or data store, with referential integrity preserved
Mask data consistently across
all your sources
-
Integrate with any data source, technology, or vendor: on-premise or in the cloud.
-
Connect to relational databases, NoSQL sources, SaaS apps, mainframe systems, message queues, flat files, XML documents, and more.
-
Ensure referential integrity through patented entity-based data masking.

See our data masking tool in action
Take a product tour of key masking workflows, step by step.
Accelerate software delivery
Mask data rapidly and reliably for compliant, up-to-date testing.
Ensure data compliance
Prevent PII exposure across all non-production environments.
Reduce operational costs
Optimize licensing costs by centralizing masking for all sources.
Secure collaboration
Confidently share data while protecting sensitive information.
INTERACTIVE PRODUCT TOUR
Data Masking
Close
Take the product tour
K2view Data Masking
Mask data from any source quickly and easily with K2view while maintaining referential integrity
EXPERIENCE OUR Synthetic Data Generation TOOL
Take the interactive product tour
Discover additional K2view products
Explore how K2view Test Data Management and Synthetic Data Generation can further enhance the way you provision, secure, and automate compliant data in your lower environments.
- Self-service portal for dev and test teams
- Cross-system data subsetting
- Subset, reserve, rollback, and age test data
- All data sources, from mainframes to SaaS apps
- AI test data provisioning from test cases
- AI-based generation for regression testing
- Rule-based generation for new functionality testing
- Entity-based cloning for load testing
- Subset, reserve, rollback, and age synthetic data
- Provision synthetic data into lower environments
Book a demo and experience AI-powered data masking
See it for yourself: From sensitive data discovery to data masking and compliant data delivery.